I was experimenting with Digest (DIGEST-MD5) authentication using SunOne Directory Server. There are not a lot of notes to explain how to use it, nor is the Sun tutorial on JNDI very helpful.
Note: Here is the important thing to remember. You can ONLY use DIGEST-MD5 with plain text passwords. For example, if the passwords are set using SSHA (Secure Salted Hashing Algorithm), you will need to change them to plain text to use it. This is not something I would recommend doing, because DIGEST-MD5 is not as secure as SSHA.
I would recommend using SSL without using DIGEST-MD5, and keep the passwords secured.
Showing posts with label LDAP. Show all posts
Showing posts with label LDAP. Show all posts
Wednesday, January 14, 2009
Saturday, September 27, 2008
OpenDS LDAP and GlassFish Configuration
Introduction
A question was posted to our JUG mailing list on how to lock a directory which contained an Adobe™ PDF file. In this example I want to cover a couple of really cool technologies, and how to implement them.
OpenDS is a project hosted on Java.net. It is an open source directory server which is based on the Sun™ SunOne™ Directory server and its predecessors (Netscape™ iPlanet™). It has a binary, or a Java™ Webstart deployment mechanism. It has a simple quick start setup including SSL based LDAP, and directory replication.
This is a simple to install, easy to use and configure, no-nosense LDAP server. It is a great server for prototyping.
Project Glassfish is an open source Java EE application server. It is simple to install and configure, and easy to use. The chances are pretty good that if you are reading this blog, you are familiar with its enormous benefits.
Case
The developer has a pdf file that is located inside a web project on the web server. The file can be bookmarked by users, but the developer wants to make sure that the user authenticates with the server before the file is displayed.
Software and Files Required
Setup
1. Download and install Glassfish
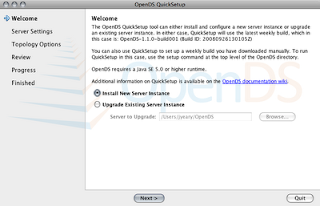
3. Create a new instance.
4. Accept the default installation directory. Set the password for the cn=Directory Manager to test.
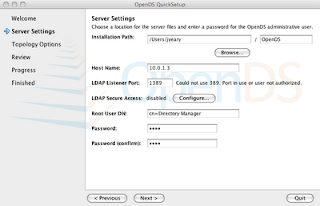
5. Press the Configure button to configure the secure LDAP connection.
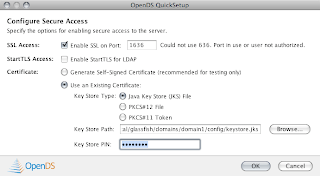
6. Select the default for topology options and continue to Directory Data Next.
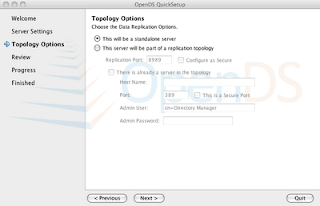
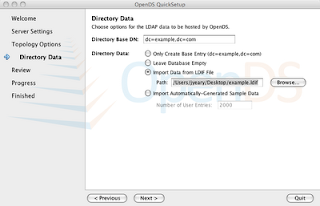
7. Review the selections and Finish.
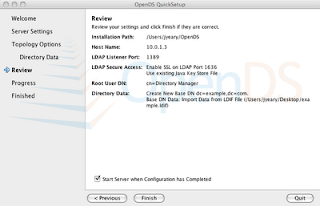
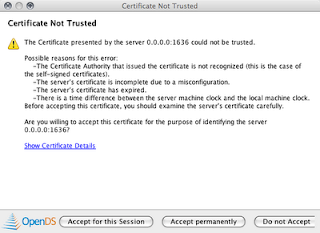
8. Authenticate with the server using cn=Directory Manager and password "test".
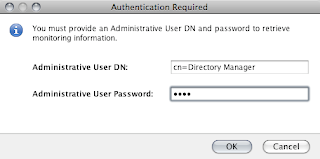
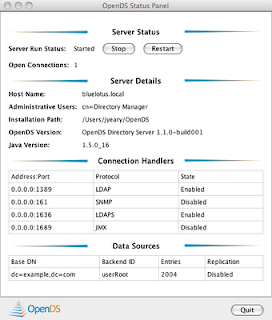
Congrats. You now have a running LDAP server.
If you want to explore the contents of the directory use a tool like JXplorer, or Apache Directory Studio.
Now we need to configure our LDAP Security Realm in Glassfish. You may have multiple realms in Glassfish to accommodate application requirements.
1. Start Glassfish and login on http://localhost:4848. The default user is admin and password is adminadmin.
2. Go to Configuration --> Security --> Realms. Create a new Realm
4. Save and you are done.
You have now configured Glassfish to use OpenDS.
Once you successfully authenticate, you will see a list of popular software that runs on Glassfish.
A question was posted to our JUG mailing list on how to lock a directory which contained an Adobe™ PDF file. In this example I want to cover a couple of really cool technologies, and how to implement them.
OpenDS is a project hosted on Java.net. It is an open source directory server which is based on the Sun™ SunOne™ Directory server and its predecessors (Netscape™ iPlanet™). It has a binary, or a Java™ Webstart deployment mechanism. It has a simple quick start setup including SSL based LDAP, and directory replication.
This is a simple to install, easy to use and configure, no-nosense LDAP server. It is a great server for prototyping.
Project Glassfish is an open source Java EE application server. It is simple to install and configure, and easy to use. The chances are pretty good that if you are reading this blog, you are familiar with its enormous benefits.
Case
The developer has a pdf file that is located inside a web project on the web server. The file can be bookmarked by users, but the developer wants to make sure that the user authenticates with the server before the file is displayed.
Software and Files Required
- OpenDS 1.x
- GlassFish Version 2 Update Release 2
- example.ldif.zip
- GlassfishSecurityExampleLDAP.zip
Setup
1. Download and install Glassfish
Note: When Glassfish is installed it creates its own self-signed SSL certificates. We will use this certificate later.2. Start the installation of OpenDS

3. Create a new instance.
4. Accept the default installation directory. Set the password for the cn=Directory Manager to test.

5. Press the Configure button to configure the secure LDAP connection.
- Set the Key Store Type to Java Key Store (JKS).
- Set the key store path to point to the keystore.jks file located in the GLASSFISH_HOME/domains/domain1/config directory.
- Set the Key Store Pin to changeit.
Note: "changeit" is the default password to the keystore. You will need to "change it" for a production system.

6. Select the default for topology options and continue to Directory Data Next.

- Directory Data should have the default Directory Base DN: dc=example,dc=com
- Select Import Data from LDIF file and use this example.ldif file. Next.
Note: I have created a pre-generated list of users previously. In this example, I have created a group and assigned it members. So to simplify the example, please use the example.ldif file.

7. Review the selections and Finish.

8. Authenticate with the server using cn=Directory Manager and password "test".


Note: A message will pop-up asking if you want to accept the certificate for the LDAP server. Use the this session only option.

Congrats. You now have a running LDAP server.
If you want to explore the contents of the directory use a tool like JXplorer, or Apache Directory Studio.
Now we need to configure our LDAP Security Realm in Glassfish. You may have multiple realms in Glassfish to accommodate application requirements.
1. Start Glassfish and login on http://localhost:4848. The default user is admin and password is adminadmin.
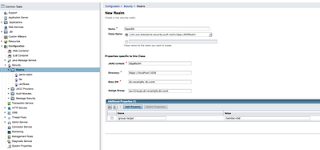
2. Go to Configuration --> Security --> Realms. Create a new Realm
- Name: OpenDS
- Class: com.sun.enterprise.security.auth.realm.LDAPRealm
- JAAS context: ldapRealm
- Directory: ldaps://localhost:1636
- Base DN: dc=example, dc=com
- Assign Group: ou=Groups,dc=example,dc=com
- group-search-filter: member=%d

Note: The group-search-filter defines the attribute to look at when determining members of the groups. It may be member, memberurl, etc. depending on how you define your groups. In the example.ldif file, I have define the group as a groupOfNames which contains member [0...] attributes. The %d format expands to match the Relative Distinguished Name (RDN).
4. Save and you are done.
You have now configured Glassfish to use OpenDS.
Note: Since we configured it to use secure LDAP, remember to configure your server to use SSL to authenticate users. Otherwise the secure LDAP portion is a waste if the users are transmitting their usernames and passwords in cleartext over the networkI have created a sample Netbeans project which takes advantage of the new LDAP authentication. The project creates a page with a link to a PDF file located in a secured directory. The directory requires the user to authenticate using basic authentication implemented in the browser. If you fail to authenticate, it will produce a 403 error. The project is located here.
Once you successfully authenticate, you will see a list of popular software that runs on Glassfish.
Sunday, March 25, 2007
Sun Java System Application Server 9.x (glassfish) External JNDI LDAP Resource Part III
I have had a question posed to me about how to use this resource once it is setup. Indeed it would be quite limiting without an example. I have created a stateless session bean (SSB) using JEE5 resource injection to show how to use it. It also has @WebService capabilities for testing. Keep in mind that the application has NO security and is merely provided as an example.
Prerequisites:
License: Apache 2.0
Package: EJBLDAPModule.zip
This is a Netbeans 6 project.
Prerequisites:
- LDAP Server installed and configured
- Sun Java System Application Server (glassfish) 9.x
- External JNDI LDAP resource configured
License: Apache 2.0
Package: EJBLDAPModule.zip
This is a Netbeans 6 project.
Thursday, March 15, 2007
Sun Java System Application Server 9.x (glassfish) External JNDI LDAP Resource Part II
In my recent blog entry on configuring an external JNDI LDAP entry, I showed how to connect to an LDAP server as a JNDI reference. This assumes that the LDAP server is on the local machine and that it allows anonymous authentication. Usually this is not the case. I will cover how to use a login to an LDAP server which requires a little more configuration.
Prerequisites:
Please follow the directions in my previous blog entry to set up the basic external JNDI resource. The Sun Java System Application Server 9.1 Administration Guide is incorrect on how to set the properties. It refers to using some properties that are defined for LDAP like PROVIDER-URL. Unfortunately, to use them you would need to prefix them with the appropriate class. So we will use an alternate tack and use them by their fully qualified names. Add the following properties to the entry.
PROVIDER-URL:
java.naming.provider.url
SECURITY_PRINCIPAL:
java.naming.security.principal
SECURITY_AUTHENTICATION:
java.naming.security.authentication
SECURITY_CREDENTIALS:
java.naming.security.credentials
Since we have the fully qualified names, we can use them to set the properties for our external JNDI resource. See the image below.

Once you have the properties set and saved, you will have a complete external JNDI LDAP connection.
Congratulations!
Prerequisites:
- A working LDAP server
- A login which can browse the directory tree
Please follow the directions in my previous blog entry to set up the basic external JNDI resource. The Sun Java System Application Server 9.1 Administration Guide is incorrect on how to set the properties. It refers to using some properties that are defined for LDAP like PROVIDER-URL. Unfortunately, to use them you would need to prefix them with the appropriate class. So we will use an alternate tack and use them by their fully qualified names. Add the following properties to the entry.
PROVIDER-URL:
java.naming.provider.url
SECURITY_PRINCIPAL:
java.naming.security.principal
SECURITY_AUTHENTICATION:
java.naming.security.authentication
SECURITY_CREDENTIALS:
java.naming.security.credentials
Since we have the fully qualified names, we can use them to set the properties for our external JNDI resource. See the image below.

Once you have the properties set and saved, you will have a complete external JNDI LDAP connection.
Congratulations!
Tuesday, March 06, 2007
Sun Java System Application Server 9.x (glassfish) External JNDI LDAP Resource Part I
I read the SJSAS Administration Guide to determine how to set up an external JNDI Resource. In my case, I wanted to simply provide another method to talk to LDAP outside of the security context. The Administration Guide is helpful...but incorrect. I have included the steps required to connect to an external LDAP server below. This works with OpenLDAP and SunONE Directory Server 5.2. The syntax should be similar on other systems.
Prerequisites:
1. Log into the glassfish administration console.
2. Navigate to the Resources --> JNDI --> External Resources tree.

3. Create a new JNDI External Resource (see image below)

4. Check to make sure that the resource was created correctly and that it appears in the server JNDI Browser. If it does, you have configured it correctly. To find the JNDI Browser go to Application Server --> JNDI Browsing.

5. You should see something that looks like the image below. Please note the organizationalUnit (ou) ou=people and ou=groups are displayed as nodes in the BaseDN.

Success!
Prerequisites:
- An LDAP server. I use both OpenLDAP and SunONE Directory Server
- Sun Java System Application Server 9.x (Project Glassfish). I am using Glassfish V2 Build 37
1. Log into the glassfish administration console.
2. Navigate to the Resources --> JNDI --> External Resources tree.

3. Create a new JNDI External Resource (see image below)
- JNDI Name: pick a unique name for the resource. I prefix mine with ldap e.g. ldap/myldap
- Resource Type: javax.naming.ldap.LdapContext
- Factory Class: com.sun.jndi.ldap.LdapCtxFactory
- JNDI Lookup: this would be your BaseDN e.g. dc=bluelotusholdings,dc=com

4. Check to make sure that the resource was created correctly and that it appears in the server JNDI Browser. If it does, you have configured it correctly. To find the JNDI Browser go to Application Server --> JNDI Browsing.

5. You should see something that looks like the image below. Please note the organizationalUnit (ou) ou=people and ou=groups are displayed as nodes in the BaseDN.

Success!
Sunday, January 28, 2007
LDAP Authentication with Apache Derby (Java DB)
It has come to my attention that there is not a really good tutorial on how to use Apache Derby and LDAP without combining a lot of different sources. Hopefully this will simplify the work for everyone wanting to use LDAP authentication with Apache Derby.
Assumptions:
Procedures:
Global:
If you want to have the configuration set on a global level add the following to a file called derby.properties in the installation directory. You will need to modify it to match your environment.
Database:
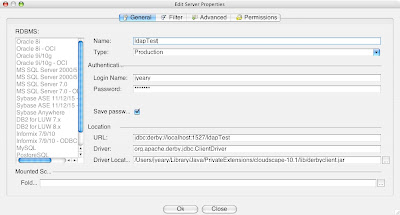
You can set the database properties on a database basis. This is accomplished by setting the parameters (database properties) in the database using SQL. The script is located below. This must be modified to accommodate your environment. Place the jndi and ldap files in the directory containing the database (see below). The database in my example is called ldaptest.
All Done!
Notes:
Assumptions:
- You have LDAP installed and configured.
- You have Apache Derby installed on your system.
- You need JNDI libraries from Sun (I am using jndi 1.2.1)
- You need LDAP libraries from Sun. (I am using ldap 1.2.4)
Procedures:
Global:
If you want to have the configuration set on a global level add the following to a file called derby.properties in the installation directory. You will need to modify it to match your environment.
derby.connection.requireAuthentication=true
derby.authentication.provider=LDAP
derby.authentication.server=ldap://localhost:389
derby.authentication.ldap.searchBase=ou=people,dc=bluelotusholdings,dc=com
derby.database.defaultAccessMode=fullAccess
Database:
You can set the database properties on a database basis. This is accomplished by setting the parameters (database properties) in the database using SQL. The script is located below. This must be modified to accommodate your environment. Place the jndi and ldap files in the directory containing the database (see below). The database in my example is called ldaptest.

Once you have executed the script above, you will need to restart the database. I used my Aqua Studio application to connect to the database.
/* Apache Derby 10.x */
/*
* This file is used to set the database-wide LDAP configuration. Rebooting the service is
* required for the changes to take effect.
*/
/* Set the authentication provider to LDAP */
CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY(
'derby.authentication.provider',
'LDAP')
/* Set the LDAP server */
CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY(
'derby.authentication.server',
'banyan:389')
/* Set the BaseDN to search */
CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY(
'derby.authentication.ldap.searchBase',
'ou=people,dc=bluelotusholdings,dc=com')
/* Create a cached entry for a user */
CALL SYSCS_UTIL.SYSCS_SET_DATABASE_PROPERTY(
'derby.user.jyeary',
'uid=jyeary,ou=people,dc=bluelotusholdings,dc=com')

All Done!
Notes:
- If LDAP is not available you can not connect to the database.
Labels:
Apache Derby
,
JavaDB
,
JNDI
,
LDAP
Subscribe to:
Posts
(
Atom
)
Popular Posts
-
Introduction This article is not another diatribe to tell you the importance of unit testing. I think we can all agree that it is important...
-
A friend of mine asked me if there was a list of reserved words in EL and JSF. He had previously looked for it, and after some Google search...
-
I saw a question posed on stackoverflow called Trouble with Primefaces 3.0.M2 SelectOneMenu Ajax behavior and I had just done an example a...
-
I was working on a couple of SSL based issues when I made a couple of observations. The default self-signed key generation in Java does not ...
-
This is an example on how to make a system call to the local operating system to execute external programs. This example was written to work...
-
We have been doing a lot of work lately with PrimeFaces. A common set of questions comes up about displaying <p:dialog/> boxes on a pa...
-
I was asked earlier today how to reset fields in a JSF application, if the validation fails. In his case, he had a Richfaces table which had...
-
Previously, I posted an example of how to use JSF 1.2 with form based authentication (j_security_check). In this example, I use JSF 2.x to...
-
Image by quasarkitten via Flickr The basics for creating a Maven archetype can be found in the Maven - Guide to Creating Archetypes . The ...
-
Abstract A common use case is to iterate over a collection of elements, and display them on a page. In the world of JSP, we would use a Ja...