Prerequisites:
- You need an account at CACert.org
- You need to install and configure Sun Java System Application Server 9.x or Project Glassfish
Instructions:
1. Go to the domains/domain
You will find two JKS keystores located in the directory. One is called cacerts.jks and the other is keystore.jks. The cacerts.jks file is used to store the Certification Authority (CA) certificates. The keystore.jks file is used to store locally generated certificates. There is a default key located in both the keystores called s1as which is created when you install the application server.
To view the certificates in the keystore use the keytool utility as follows
keytool -list -v -keystore keystore.jks -storepass changeit
This will display the certificates in the keystore.
2. Import the CACert.org root (class 1) and class 3 certificates from here. Select the PEM format files and save them to the local drive.
NOTE: You will want to import these files into both the cacerts.jks and keystore.jks files. You will need the files in your keystore.jks file to import the signed certificate later.
Import the files as follows:
keytool -import -v -alias cacert -trustcacerts -keystore cacerts.jks -storepass changeit -file root.crt
keytool -import -v -alias cacert -trustcacerts -keystore keystore.jks -storepass changeit -file root.crt
keytool -import -v -alias cacert3 -trustcacerts -keystore cacerts.jks -storepass changeit -file class3.crt
keytool -import -v -alias cacert3 -trustcacerts -keystore keystore.jks -storepass changeit -file class3.crt
3. Create a new certificate for the server using the following
keytool -genkey -keyalg RSA -alias server -keystore keystore.jks -keypass changeit -storepass changeit -noprompt -v -dname "cn=yourdomain.com, ou=Sun Java System Application Server, o=your company name, s=your state, c=your country"
Change the dname values as appropriate. Afterwards check the keystore.
keytool -list -v -alias server -keystore keystore.jks -storepass changeit
You should get an output similar to this accounting for your domain:
Alias name: server Creation date: Dec 24, 2006 Entry type: keyEntry Certificate chain length: 1 Certificate[1]: Owner: CN=yourdomain.com, OU=Sun Java System Application Server, O=your company name, ST=your state, C=your country Issuer: CN=yourdomain.com, OU=Sun Java System Application Server, O=your company name, ST=your state, C=your country Serial number: 458ed092 Valid from: Sun Dec 24 14:10:10 EST 2006 until: Sat Mar 24 15:10:10 EDT 2007 Certificate fingerprints: MD5: 0D:62:DA:52:34:DE:65:40:C5:34:DB:97:EE:58:20:22 SHA1: 2B:AA:0F:A0:6D:C6:DE:C2:20:19:72:85:97:B1:6B:DA:B5:7D:AC:D0
4. Create the Certificate Signing Request (CSR) using the following command:
keytool -certreq -v -alias server -keystore keystore.jks -storepass changeit -file server.csr
5. Copy the contents of the file to the CSR request form on the CACert.org site.
Here is an example of the data in the server.csr file
-----BEGIN NEW CERTIFICATE REQUEST----- MIIBzzCCATgCAQAwgY4xFTATBgNVBAYTDHlvdXIgY291bnRyeTETMBEGA1UECBMKeW91ciBzdGF0 ZTEaMBgGA1UEChMReW91ciBjb21wYW55IG5hbWUxKzApBgNVBAsTIlN1biBKYXZhIFN5c3RlbSBB cHBsaWNhdGlvbiBTZXJ2ZXIxFzAVBgNVBAMTDnlvdXJkb21haW4uY29tMIGfMA0GCSqGSIb3DQEB AQUAA4GNADCBiQKBgQCETXJQCNJz9rDLBuE8RBV/IK4sfVt1MC0DJLd6Ph94uTy+kz9mkVml41KV zd9UORdp4VCFXd9ssS5UiophTvHzcntJpAVONTwjUkdaukYA5bE5HrKsS7BjdnJTYnoeUHJ6g1ig 6NrUt2GouQGQYeiIUCoPfXsB9g8+S/0tPI6X/wIDAQABoAAwDQYJKoZIhvcNAQEEBQADgYEAYjAR My7nevIe3HM2NrilO29ls1PrjP4h6ApppCdaGrvn8RlSaXp4kPIb5s1/vHWbIB6CIeSZvlmXk2NG 649iTBK6+wLw0RTotcQXtCx7S9YnguBeWBA+zb2fJRfdWYJhCwbm9cyAfJbP80N3lyB7/XKyvq/N fjqp30oTQiiq75U=
-----END NEW CERTIFICATE REQUEST-----
5. You should get an immediate response on the site as well as an email with the certificate located in it. Copy the certificate from the site and save it in a file called signed.crt. The file should contain something that looks like the following.
-----BEGIN CERTIFICATE-----
MIIEYjCCAkqgAwIBAgIDAwmZMA0GCSqGSIb3DQEBBQUAMHkxEDAOBgNVBAoTB1Jv
b3QgQ0ExHjAcBgNVBAsTFWh0dHA6Ly93d3cuY2FjZXJ0Lm9yZzEiMCAGA1UEAxMZ
Q0EgQ2VydCBTaWduaW5nIEF1dGhvcml0eTEhMB8GCSqGSIb3DQEJARYSc3VwcG9y
dEBjYWNlcnQub3JnMB4XDTA2MTIyNDE3MDQxNVoXDTA3MDYyMjE3MDQxNVowIDEe
MBwGA1UEAxMVYmx1ZWxvdHVzaG9sZGluZ3MuY29tMIGfMA0GCSqGSIb3DQEBAQUA
A4GNADCBiQKBgQChU0hgVKaULE1W7gDLGaKwmhRXBqUgH7pboozXO61eT6rOwHPi
dEBjYWNlcnQub3JnMB4XDTA2MTIyNDE3MDQxNVoXDTA3MDYyMjE3MDQxNVowIDEe
MBwGA1UEAxMVYmx1ZWxvdHVzaG9sZGluZ3MuY29tMIGfMA0GCSqGSIb3DQEBAQUA
A4GNADCBiQKBgQChU0hgVKaULE1W7gDLGaKwmhRXBqUgH7pboozXO61eT6rOwHPi
dEBjYWNlcnQub3JnMB4XDTA2MTIyNDE3MDQxNVoXDTA3MDYyMjE3MDQxNVowIDEe
MBwGA1UEAxMVYmx1ZWxvdHVzaG9sZGluZ3MuY29tMIGfMA0GCSqGSIb3DQEBAQUA
A4GNADCBiQKBgQChU0hgVKaULE1W7gDLGaKwmhRXBqUgH7pboozXO61eT6rOwHPi
5lWu+N26F+Y0xopIhlechSByXXtwwh2bX5cgock0MHBP0qvwx6pNYglqWArxbnoV
qFoNewxtkM6Riu0uYU31jZadzO7dP8ZR/CrF4AlZ8DKU7I7faWFu5HK0YwIDAQAB
o4HPMIHMMAwGA1UdEwEB/wQCMAAwNAYDVR0lBC0wKwYIKwYBBQUHAwIGCCsGAQUF
BwMBBglghkgBhvhCBAEGCisGAQQBgjcKAwMwCwYDVR0PBAQDAgWgMDIGCCsGAQUF
BwEBBCYwJDAiBggrBgEFBQcwAYYWaHR0cDovL29jc3AuY2FjZXJ0Lm9yZzBFBgNV
HREEPjA8ghVibHVlbG90dXNob2xkaW5ncy5jb22gIwYIKwYBBQUHCAWgFwwVYmx1
ZWxvdHVzaG9sZGluZ3MuY29tMA0GCSqGSIb3DQEBBQUAA4ICAQCTOLgns8xTkgwC
YozYkLqFN+bc6zmR+iu9yWY59Ayu0xR+4e9nxqfm1SsHaKo/1tQX3CyBVGm4MhMg
9uA2sNhjJPPy7y/2oafK2R6olHHkVsLfX6MXddRPNzyjQeGgxeH9FtPz9fd9b3OP
z2fAdCSgeOhH9bn2myvRPAcX7X/wh89Gmybg52jlhl6wgumg1SQlyQ60Ht4zZYyL
7Viu6WWsCPHAWUTLQ1k7XdgLDAY0JMwRBMkCCT0w7CVdC1PkGe2WTsgnEB5RHTF5
c1fQ+fiiJC+giEMI/YwfV0AkSF9ILhm/y9DDdQ6KjkxdQne3WxaUek7cm1H/xdM9
QLBkfyNfLDanySS7dDTZK28pSSItYedpzOGIQHsDY3LfSv1kdqTEEwVGZDXW6OO5
/v/efWTLn6weuypTMVrXWZ4ednz09WP5BQ7RZjPmUX8sE+IZ3SRycCH6cZERp+dN
D3UZYBuRmQ5rWx32XNDf9wY2AiuSWFvWGnDQmpjfCAi47Q4wugk7y63xl7b+LAJC
Bp5YNJnD4zFWgvMPxo8IeJk+Dd0sNcEPAd/VJH9jymqaTbx3Dv9W5ZwGxmdNv7em
3h3544G4dVuuq24ZDbCeFdLVUcS+74407fIBHMgCf3fRXCBhJbaL90srZSAV3sX3
g7DyVvIlt035V+MMwdjgg3wmF55tww==
-----END CERTIFICATE-----
6. We imported the CACert.org certificates so that we could do the next step without issues. We will want to import the new certificate to the keystore and combine it with our private key. We do this by using the same alias we assigned to the private key (keyEntry).
keytool -import -v -trustcacerts -alias server -keystore keystore.jks -keypass changeit -storepass changeit -file signed.crt
7. Delete the cacert and cacert3 certificates from the keystore.jks
keytool -delete -v -alias cacert -keystore keystore.jks -storepass changeit
keytool -delete -v -alias cacert3 -keystore keystore.jks -storepass changeit
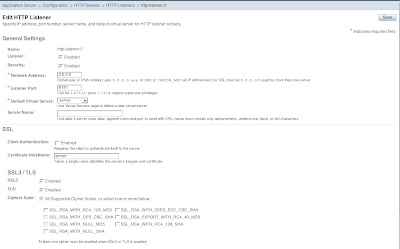
8. Configure the application server to use the new key. I try it on the HTTP Service --> HTTP Listeners --> http-listener-2. Select the security enabled, SSL3, TLS, and All supported ciphers checkboxes. Fill in the Certificate Nickname as server. Save and restart the application server.
9. Check the configuration by going to https://localhost:8181
FINISHED
Congratulations you are on SSL. Once I am sure that everything is working, I immediately set the admin site to use SSL/TLS as an important security measure.